Intrusion Detection And Virus Network Diagram
Free Printable Intrusion Detection And Virus Network Diagram

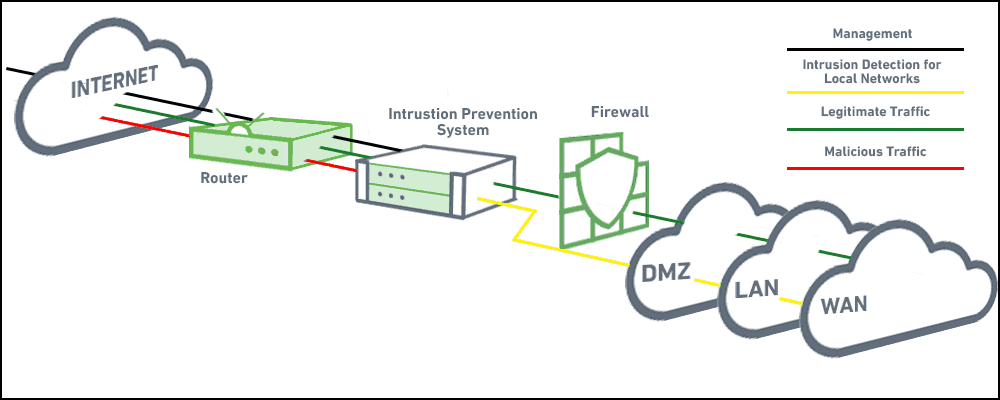
A combination of a ???rewall and intrusion detection.
Intrusion detection and virus network diagram. In fact you can think of ips as an extension of ids because an ips system actively disconnects devices or connections that are deemed as being used for. An intrusion detection system ids is a type of security software designed to automatically alert administrators when someone or something is trying to compromise information system through malicious activities such as ddos attacks or security policy violations. Use one or more diagrams to describe all the actors in design session problem and how they will interact with the use cases of your system. Let us know what you think.
Provide flow of events for all of your use cases. Like a virus detection system misuse detection software is only as good as the database of attack signatures that it uses to compare packets against. It checks each and every packet that is entering the network to make sure it does not contain any malicious content which would harm the network or the end system. In cloud environments this is traf???c already permitted by the security group.
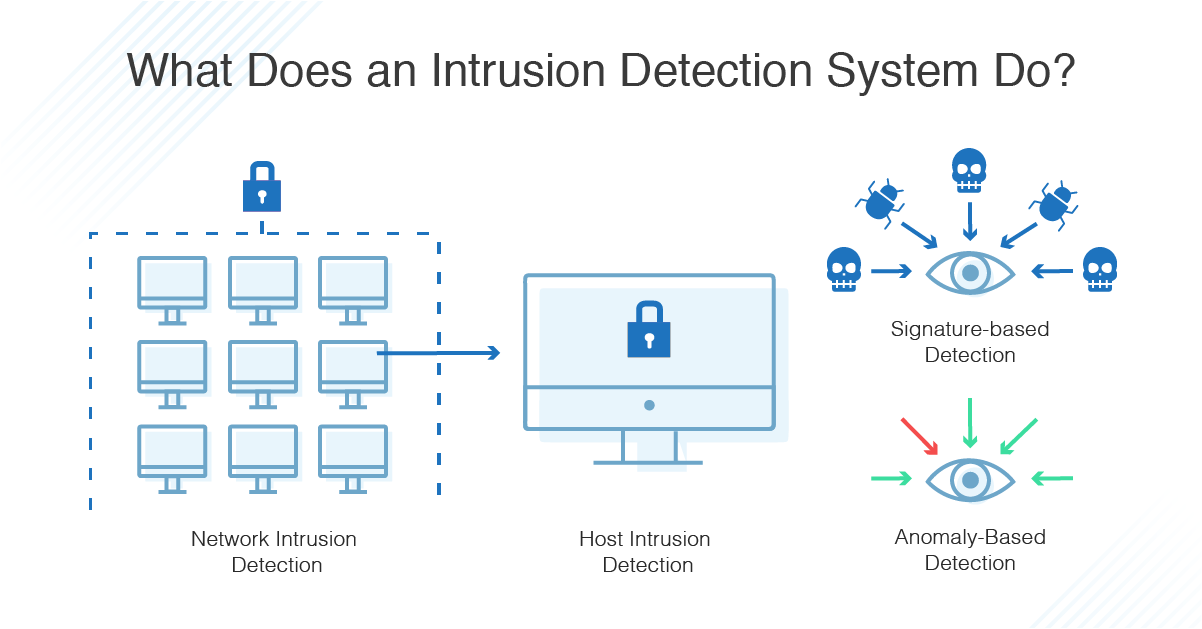
An intrusion detection system ids is a device or software application that monitors a network or systems for malicious activity or policy violations. Siem ips intrusion prevention system and antivirus. Network intrusion detection system sniffs the network traffic. Use case diagrams and use cases.
It inspects all the inbound and outbound network activity. Network intrusion detection system read the following problem statement and perform the following. An ids works by monitoring system activity through examining vulnerabilities in the system the integrity of files and analyzing. An intrusion detection system ids is yet another tool in the network administrator s computer security arsenal.
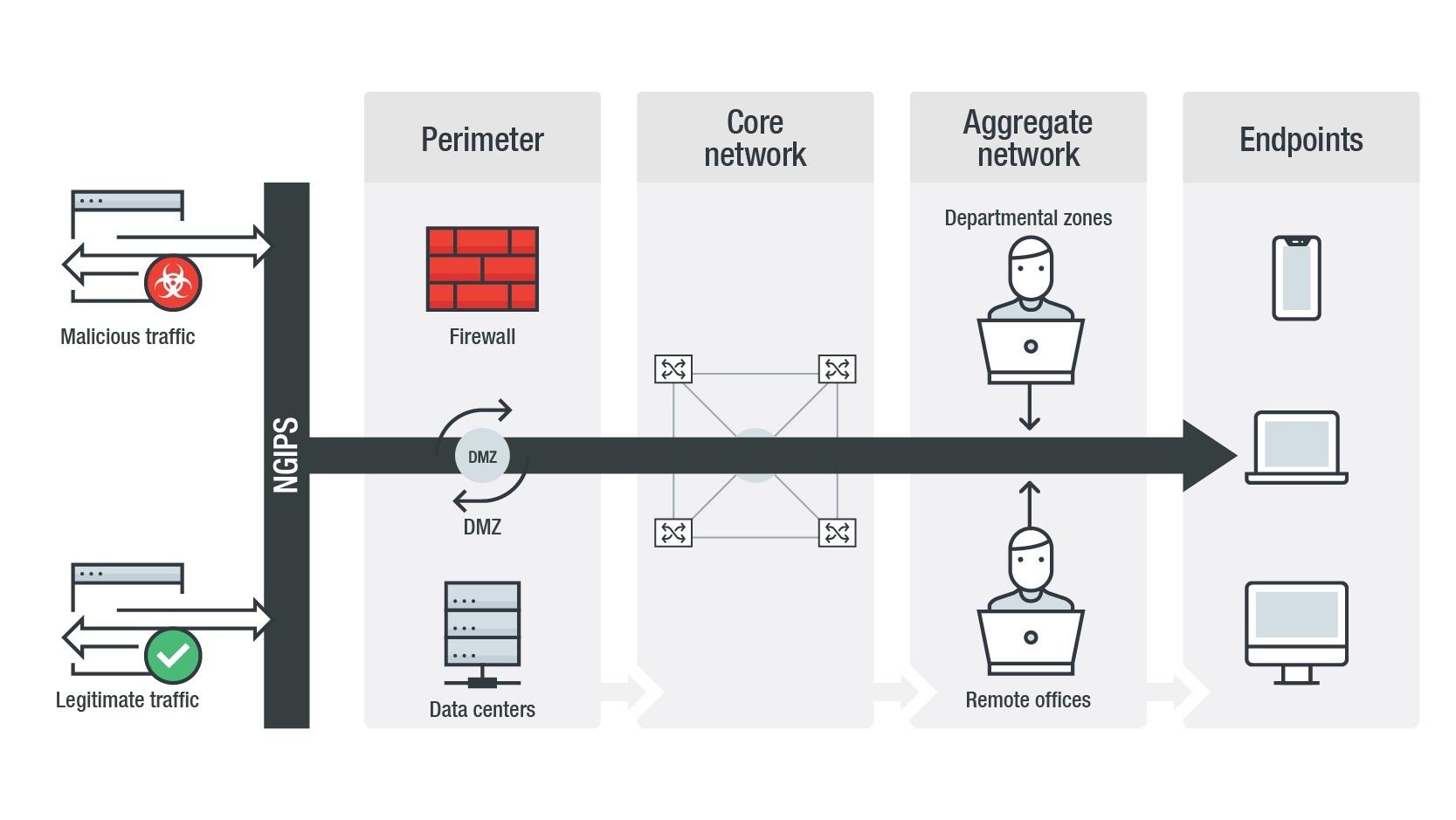
The implementation of one of the following is discussed. A siem system combines outputs from multiple sources and uses alarm. The ids identifies any suspicious pattern that may indicate an attack the system and acts as a security check on all transactions that take place in and out of the system. Intrusion detection systems ids and intrusion prevention systems ips are security measures deployed in your network to detect and stop potential incidents.
About antivirus introduction anomaly intrusion detection system a ids is a significant portion of cyber security countermeasure that exists in almost all the latest security devices. It analyses the network traf???c for signs of mali cious activity. 1 1 2 network intrusion detection system a network intrusion detection system nids provides protection in areas a ???rewall does not cover. Help us improve your experience.
Do you have time for a two minute survey. In anomaly detection the system administrator defines the baseline or normal state of the network s traffic load breakdown protocol and typical packet size. A network based intrusion detection system nids 1 monitors and detects any suspicious activity on a network. Here the security devices which are used by a ids in the systems have been discussed.