Network Diagram Utilizing Ids
Free Printable Network Diagram Utilizing Ids

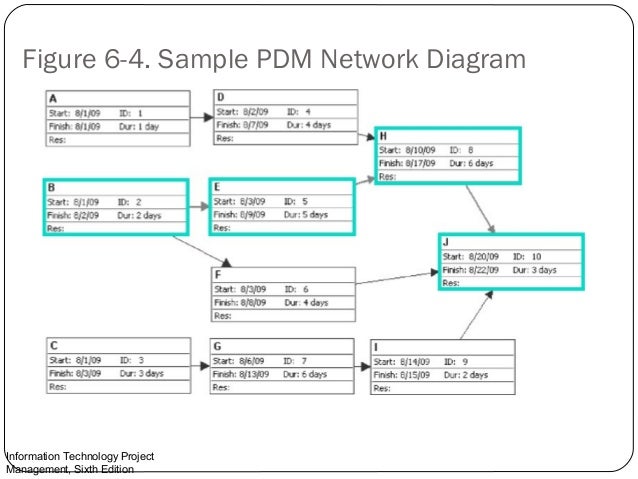
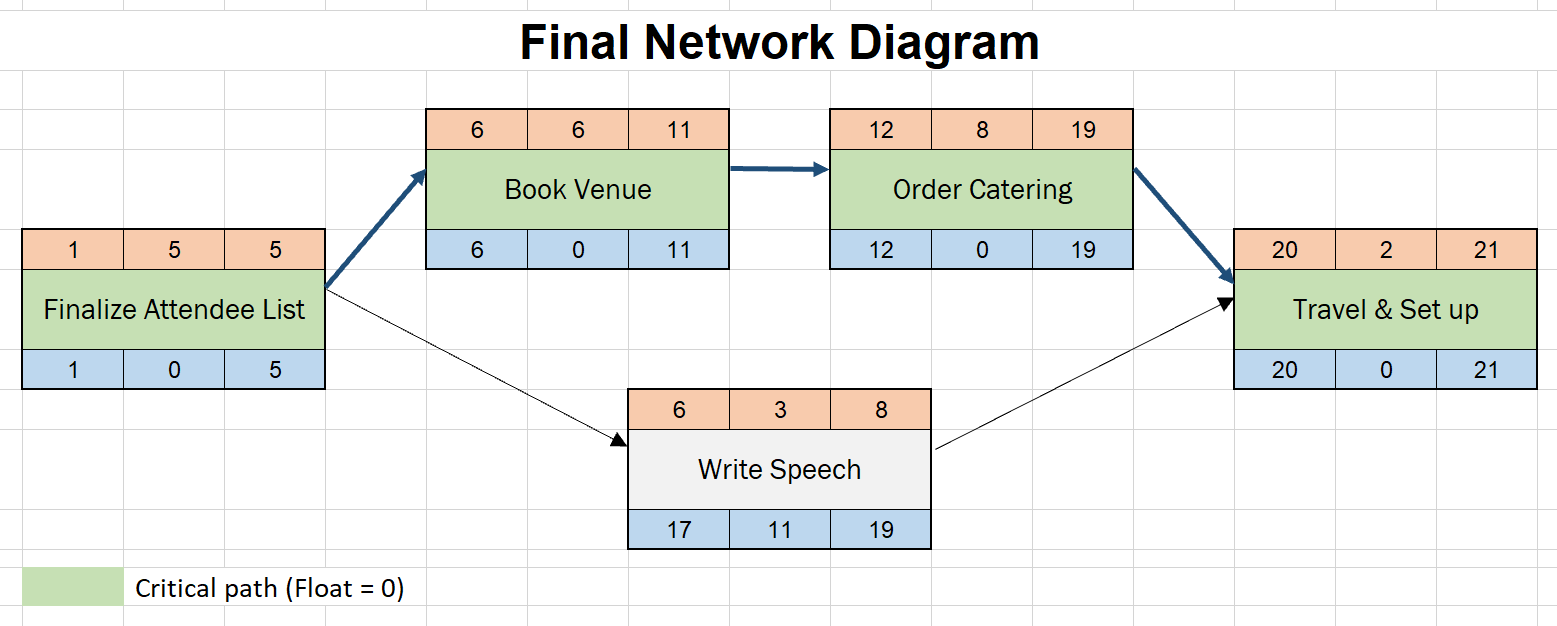
In the sequence activities process of project time management the major output is a network diagram but what is a network diagram.
Network diagram utilizing ids. Tidygraph provides a way to create a network object that more closely resembles a tibble or data frame. Flowchart maker and online diagram software. I want to create a network by using r but i only have a table that contain otu id and the abundance value of two samples only. Therefore logical network diagrams typically show subnets including vlan ids masks and addresses network devices like routers and firewalls and routing protocols.
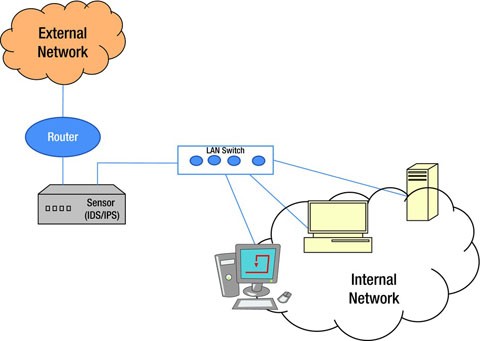
A network diagram will help us focus in on the activity relationships. An intrusion detection system ids is a device or software application that monitors a network or systems for malicious activity or policy violations. If can which package can be used or any other software. Draw io can import vsdx gliffy and lucidchart files.
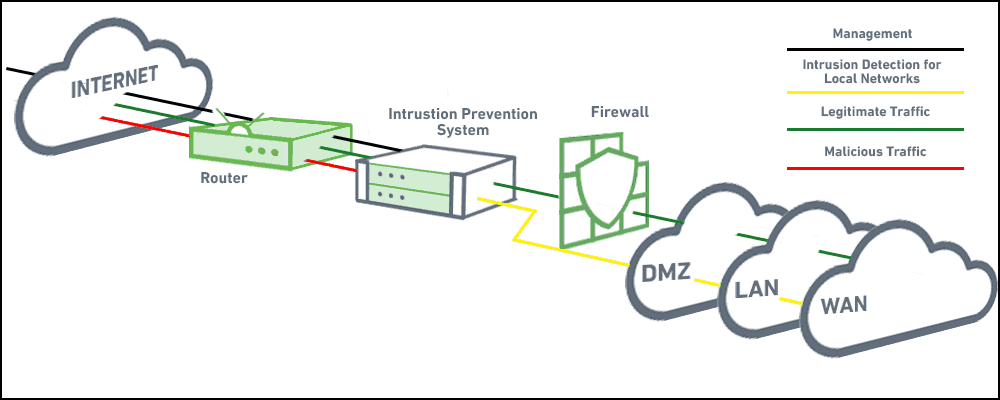
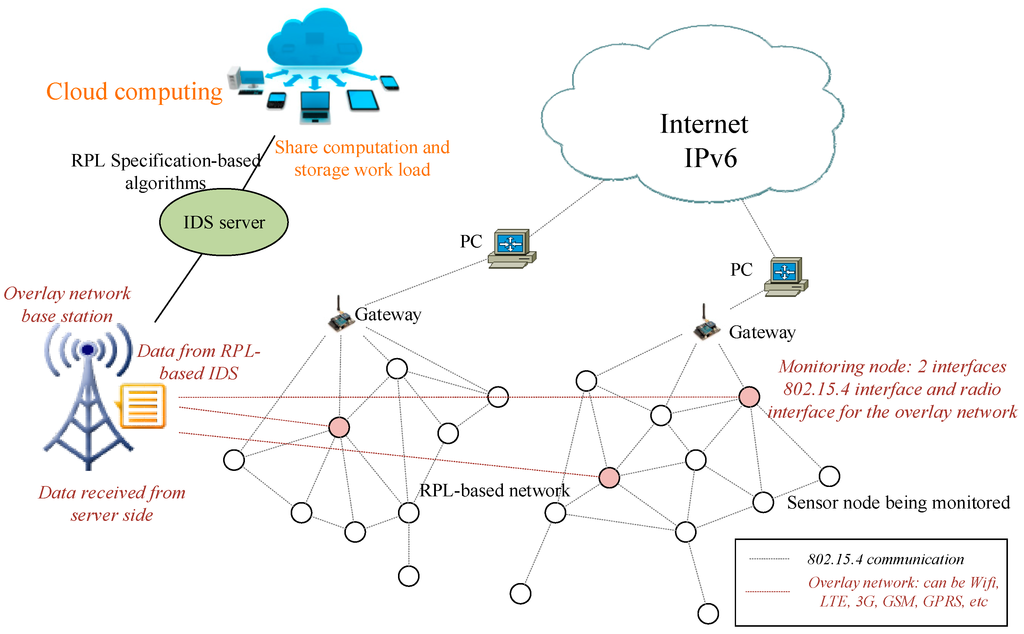
Image visualizing the anomaly data from the normal using matplotlib library. In the online pmp training its purpose is explained as visualizing the project activities in boxes with the activity ids and showing the interrelationship of activities with arrows network diagrams tell if an activity will start before after or at the same. I should mention that at the beginning of our project we had researched quite a few papers on intrusion detection systems using machine learning techniques and we discovered that not one of them utilized the iscx 2012 data set most likely due to its unavailability at the time. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management siem system.
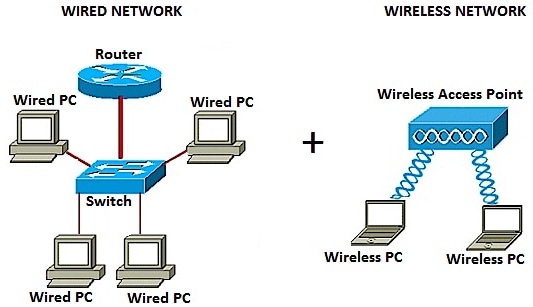
Network interfaces allowing replayed packets to be injected into different points on a network based on the source address 9. To display a network diagram of the schedule select the task tab view ribbon group gantt chart drop down menu and network diagram figure 2. A network diagram can be either physical or logical. A siem system combines outputs from multiple sources and uses alarm.
You can use it as a flowchart maker network diagram software to create uml online as an er diagram tool to design database schema to build bpmn online as a circuit diagram maker and more. An id system gathers and analyzes information from diverse areas within a computer or a network to identify possible security breaches which include both intrusions attack from outside. Construction of network diagrams by using r. Intrusion detection system ids intrusion detection id is the process of monitoring for and identifying attempted unauthorized system access or manipulation.
2 9 years ago by. A logical network diagram describes the way information flows through a network. The network diagram for our demonstration project is displayed in figure 3.