Network Security Applications Diagram Sec
Free Printable Network Security Applications Diagram Sec

Application security encompasses the hardware software and processes you use to close those holes.
Network security applications diagram sec. Unfortunately any application may contain holes or vulnerabilities that attackers can use to infiltrate your network. Get full access to the sec network and sec network plus including live games and programs such as sec nation and the paul finebaum show. Unified threat management utm is an approach to information security where a single hardware or software installation provides multiple security functions. As a benchmark for best practices in it security this certification covers the essential principles for network security and risk management making it an important stepping stone of an it security career.
Network security is the set of actions adopted for prevention and monitoring the unauthorized access ensuring information security and defense from the attacks protection from misuses and modification of a network and its resources. The comptia security certification exam will verify the successful candidate has the knowledge and skills required to assess the security posture of an enterprise environment and recommend and implement appropriate security solutions. It is a wireless network security standard that tries to make a virtual private network is tunneled through a wide area ne voip is basically a telephone connection over the internet. Which of the following is the best solution for the network administrator to secure each internal website.
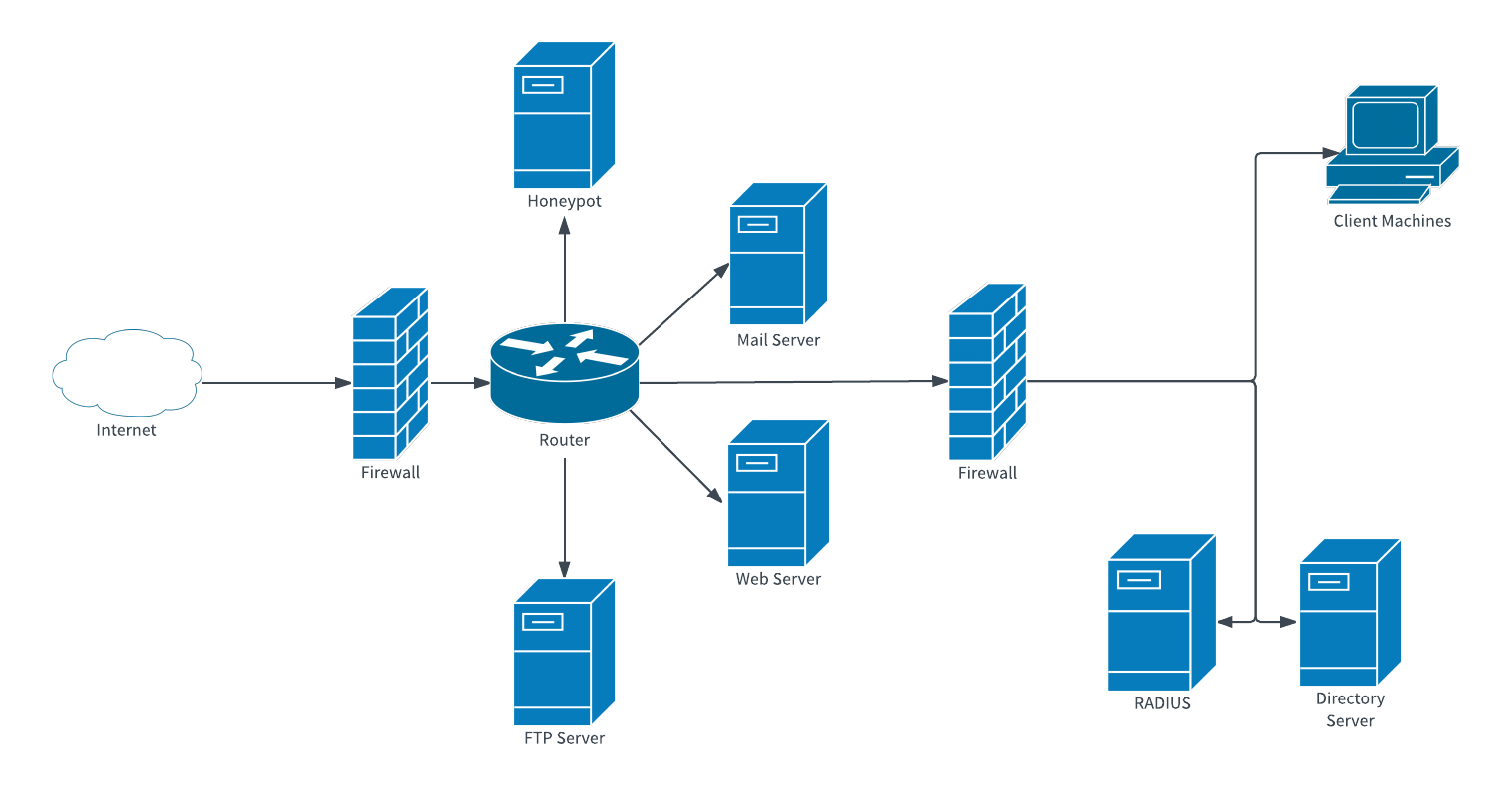
750 on a scale of 100 900 recommended experience. Network security architecture diagram visually reflects the network s structure and construction and all actions. The chief security officer cs0 has issued a new policy that requires that all internal websites be configured for https traffic only. Operate with an awareness of.
Utm simplifies information security management by providing a single management and reporting point for the security administrator rather. Network security architecture diagram. 90 minutes passing score. The network administrator has been tasked to update all internal sites without incurring additional costs.
Comptia network certification and two years of technical networking experience with an emphasis on security. They ll collect logs from routers and switches and firewalls and intrusion prevention systems and servers and application devices and anything else that can provide them with information about what s happening on the network. This contrasts with the traditional method of having point solutions for each security function. Monitor and secure hybrid environments including cloud mobile and iot.
Most security professionals will gather as much information about what s going across the network as possible. Application data and host security.