Nist Security Controls Network Diagram
Free Printable Nist Security Controls Network Diagram
Nist special publication 800 53 rev.
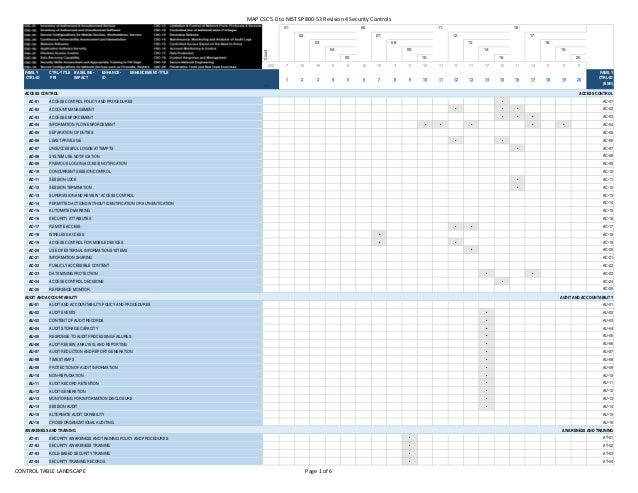
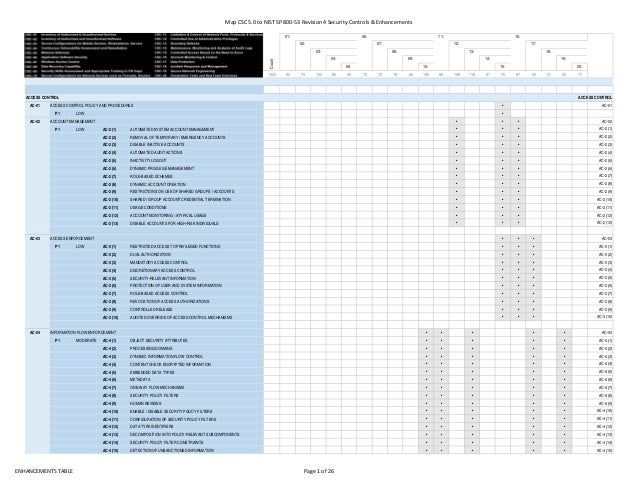
Nist security controls network diagram. Providing a stable yet flexible catalog of security controls for systems to meet current organizational protection needs and the demands of future. Federal energy regulatory commission s cybersecurity incentives policy white paper draft which discusses potential incentives to encourage utilities to go above and beyond mandated cybersecurity measures. This nist sp 800 53 database represents the security controls and associated assessment procedures defined in nist sp 800 53 revision 4 recommended security controls for federal information systems and organizations. Cnss instruction 1253 provides similar guidance for national security systems.
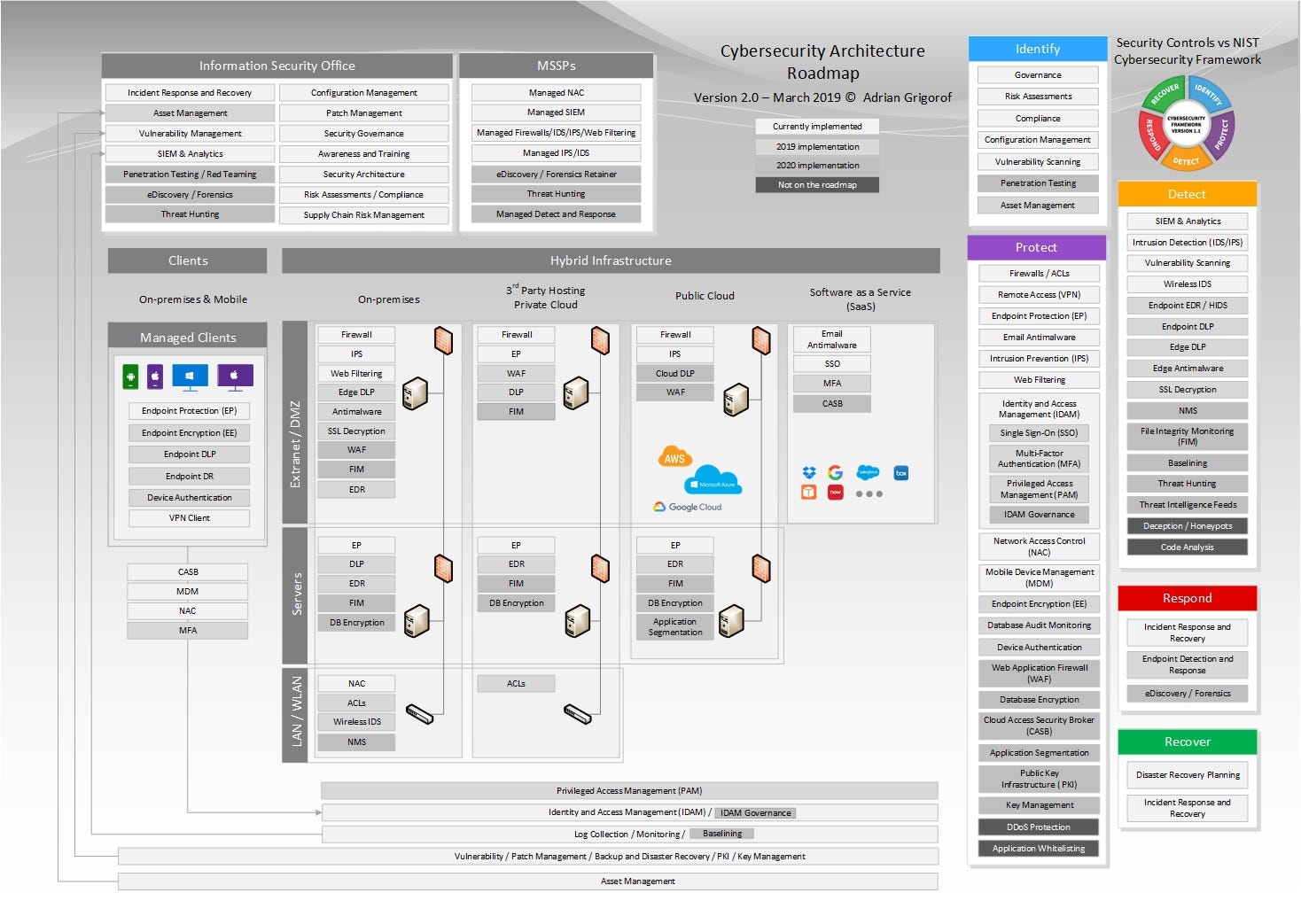
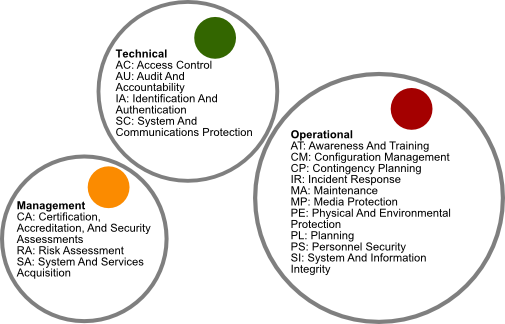
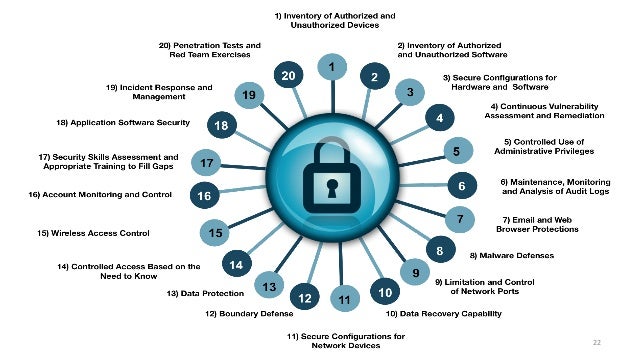
The cyber and network security program addresses nist s statutory responsibilities in the domain and the near and long term scientific issues in some of the building blocks of it and network security cryptography security testing and evaluation access control internetworking services and protocols domain name system border gateway. Cm 8 is the section in the nist security control catalog that describes what to do to meet id am 1 and id am 2. Nist security control catalog. Supplemental guidance this control addresses actions taken by organizations in the design and development of information systems.
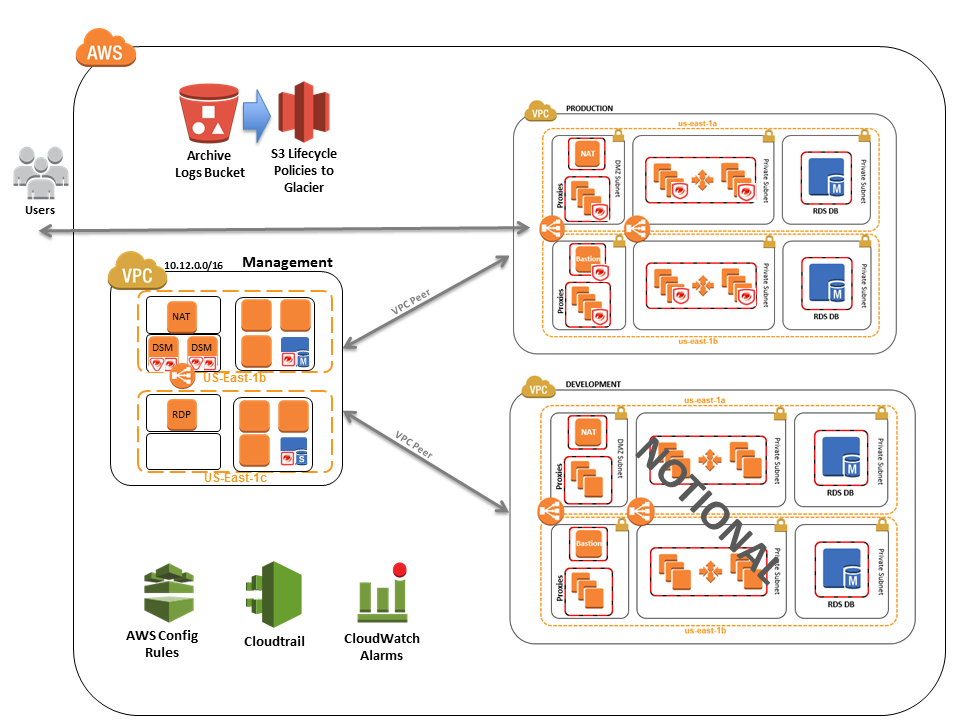
You can see how the architecture and components described in this article can meet each point in cm 8 which are referenced below. This control enhancement protects network addresses of information system components that are part of managed interfaces from. The private or leased line is the pipe that connects the it systems. Organizations or is leased from a third party e g an integrated services digital network isdn t1 or t3 line.
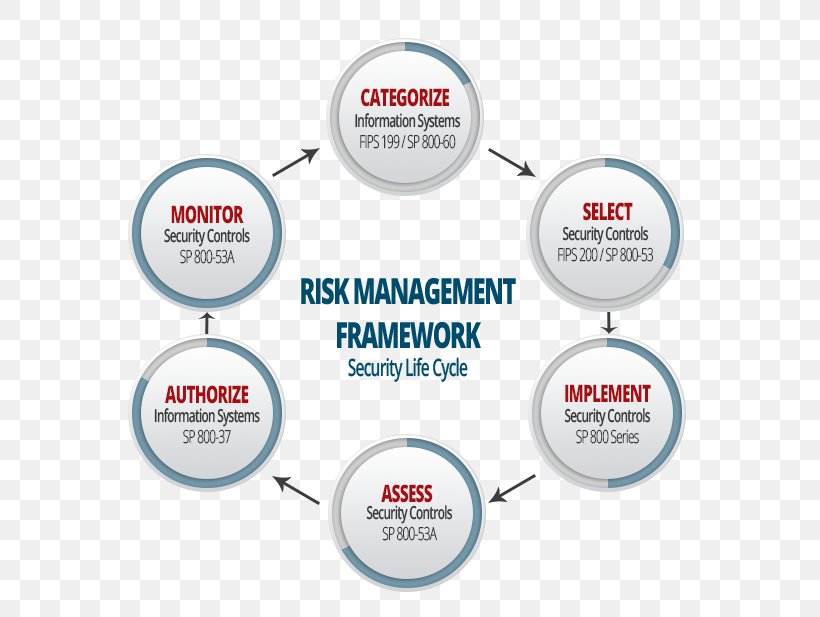
Providing a recommendation for minimum security controls for systems categorized in accordance with fips 199 standards for security categorization of federal information and information systems. Check out the csf critical infrastructure resources newest addition. Nist special publication 800 37 revision 2 provides guidance on authorizing system to operate. Our latest success stories from the government of bermuda and saudi aramco help us to demonstrate.
The information security architecture at the individual information system level is consistent with and complements the more global organization wide information security architecture described in pm 7 that is integral to and developed as part of the enterprise. Nist special publication 800 53a revision 4 provides security control assessment procedures for security controls defined in nist special publication 800 53.