Palo Alto Network Diagram Dmz Inside Outside
Free Printable Palo Alto Network Diagram Dmz Inside Outside

Finally commit all the configuration by clicking commit from right top corner.
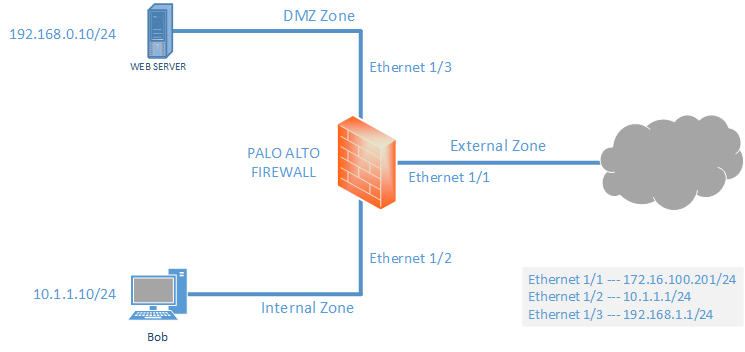
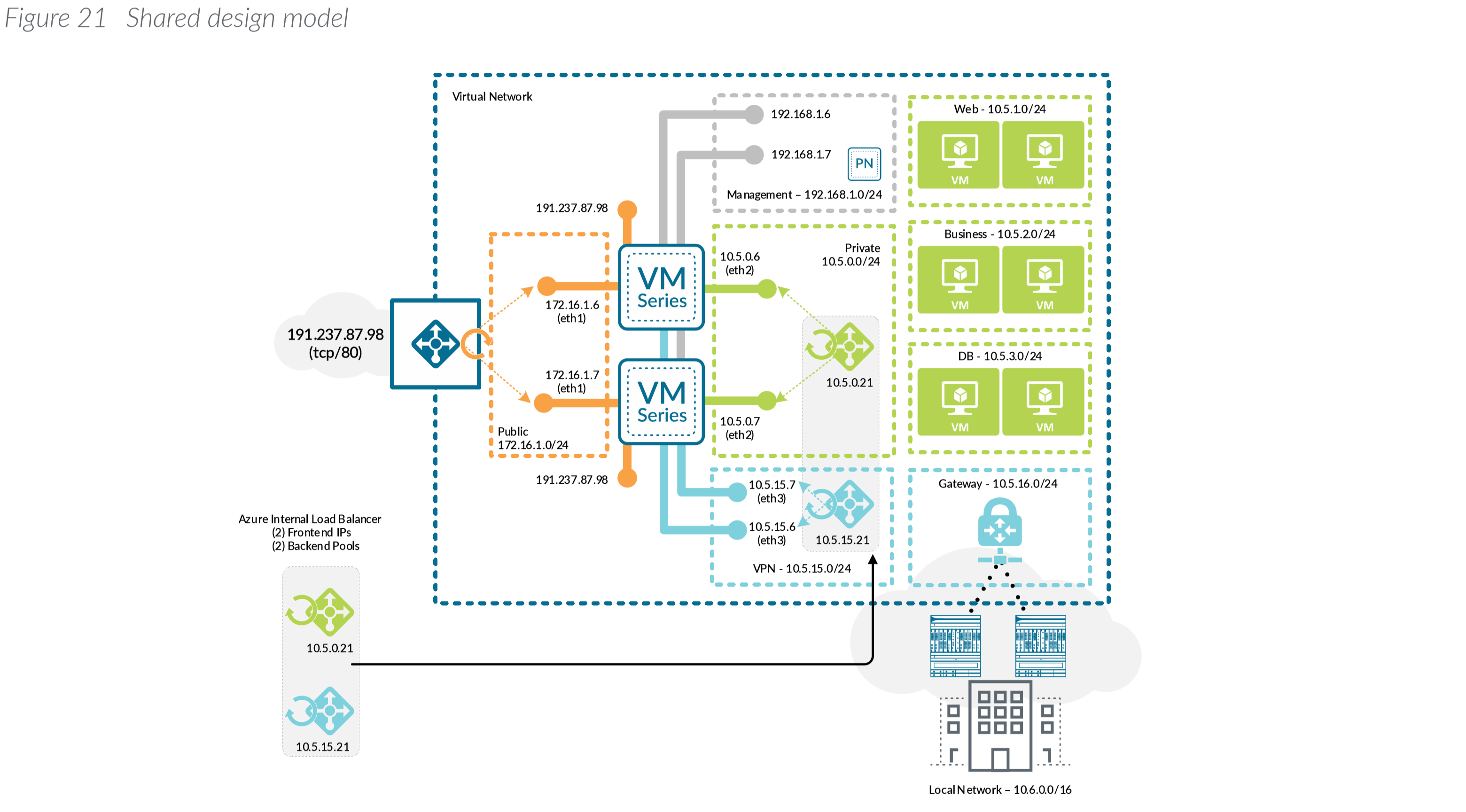
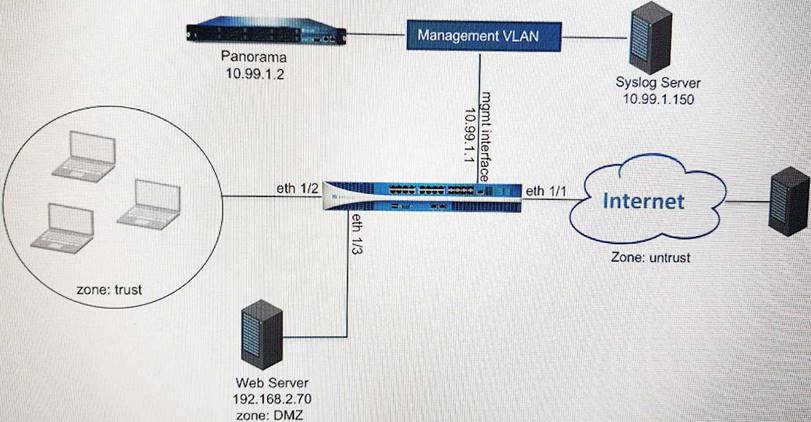
Palo alto network diagram dmz inside outside. Similarly we need to do the same steps for internal and dmz zone to add ip addresses for them. One to one nat is termed in palo alto as static nat. The palo alto firewall serves as the main layer 3 gateway so the switch is just passing all traffic to the firewall. In our lab 10 1 1 1 24 is internal interface ip and 192 168 1 1 24 is dmz interface ip.
So dmz in earlier blog palo alto to internet we configure how to allow users to go to the internet. An internal user connecting to this same fqdn connects to the external address though the physical server may be located on that user s internal subnet or a dmz with internal addressing. Outside interface vment0. Reaching internet from internal zone.
Users can bypass the palo alto networks pan firewall security profiles by using vpn or a web proxy. Inside interface vmnet2. The lab subnet is obscured and is not propagated within the network. The third rule is to decrypt ssh only traffic source from the inside zone going to the dmz.
Hi due my self training on palo alto vm i have face some issue where i m not able to ping internet but able to ping next host on same subset my pc. Since the outside interface replies to icmp from the l3 switch and palo alto device but not the dmz host i would go through any possible routing related configurations on the devices involved and also confirm that the actual dmz host is configured with a default gateway so that it can reach the asa i presume it has a gateway set since it. To enable clients on the internal network to access the public web server in the dmz zone we must configure a nat rule that redirects the packet from the external network where the original routing table lookup will determine it should go based on the destination address of 203 0 113 11 within the packet to the actual address of the web server on the dmz network of 10 1 1 11. Understand how nat is being handled by the firewall.
So today i will show you how to allow your customer to come inside to your ftp server first i configure my ethernet 1 1 with the public ip address 37 76 249 42 go to networks interface ethernet edit. Since we use two or more layers of firewalls we can put our dmz for intermediate security zones in different places in our network. For all nat processes the firewall reads the. Lets gather together the different options and consider the merits or not and sometimes how they self build.
Palo alto networks enables your team to prevent successful cyberattacks with an automated approach that delivers consistent security across cloud network and mobile. In modern enterprise networks you typically have many clusters of firewalls protecting assets in your network. When setting up nat rules the source and destination zones need to be configured to correspond to the zones to which the source and destination ip.