Standard Network Sha2 Cert Diagram
Free Printable Standard Network Sha2 Cert Diagram

Sha 1 as we mentioned earlier is now deprecated.
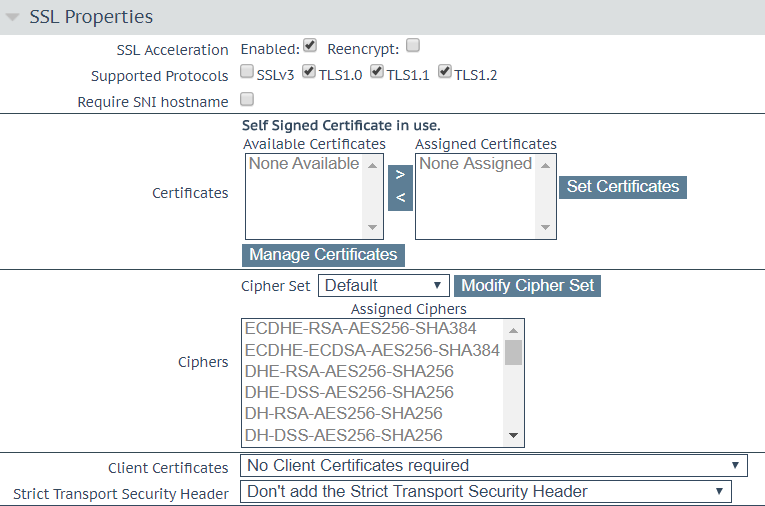
Standard network sha2 cert diagram. Generate new csrs for each sha 1 certificate. A cipher suite is a collection of ciphers and algorithms that are used for ssl tls connections. It was designed to overcome the security vulnerabilities in the sha 1 algorithm. Sha handles the hashing aspects.
Chrome shows sha 1 warnings for sites using sha 1 certificates. Sha 2 secure hash algorithm 2 is a set of cryptographic hash functions designed by the united states national security agency nsa and first published in 2001. Sha 2 is actually a family of hashes and comes in a variety of lengths the most popular being 256 bit. They are built using the merkle damg??rd structure from a one way compression function itself built using the davies meyer structure from a classified specialized block cipher.
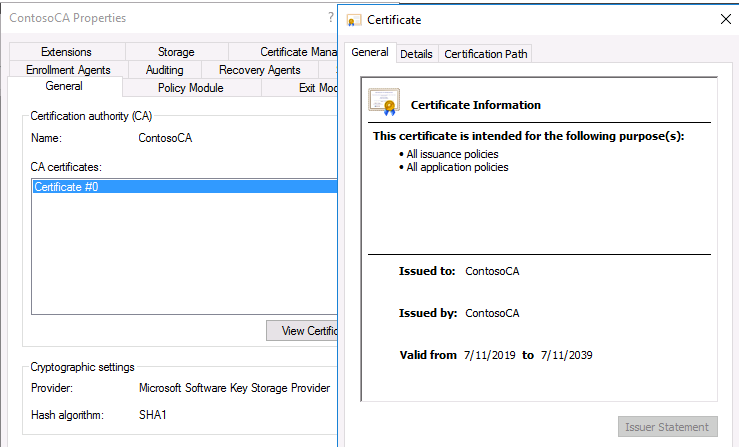
A root certification authority ca is the top of a public key infrastructure pki and generates a self signed certificate. Sha 2 is a family of four hash functions. If parts of your environment will not support sha 2 you must replace or upgrade those pieces before you can implement new certificates. Godaddy and most other cas use sha 2 or sha256 as the default certificate signature algorithm.
Choose sha 1 signature algorithm if a version older than 8 2 5 or 8 4 1 is used. If you see sha 2 sha 256 or sha 256 bit those names are referring to the same thing. In cryptography sha 1 secure hash algorithm 1 is a cryptographic hash function which takes an input and produces a 160 bit 20 byte hash value known as a message digest typically rendered as a hexadecimal number 40 digits long. Entrust ssl certificates powered by sha 2 security developed by the national institute of standards and technology nist sha 2 represents the most current set of cryptographic hash functions at a micro level sha 2 is based on a set of four hash functions 224 256 384 or 512 bits which strengthens the original sha 1 hash function released in 1995 by the nist.
Federal information processing standard. Return to top. The nist standard sha 2 was designed by the u s. It was designed by the united states national security agency and is a u s.
In november 2013 microsoft announced that it would stop trusting sha 1 certificates due to concerns that the algorithm is no longer secure. Sha 2 is now mandatory. Find all sha 1 certificates. Issuing cas are typically online and used to issue certificates to client computers network devices mobile devices and so on.
Sha 1 is a 160 bit hash. Sha 2 includes significant changes from its. This means that the root ca is validating itself self validating. National security agency and published in 2001.
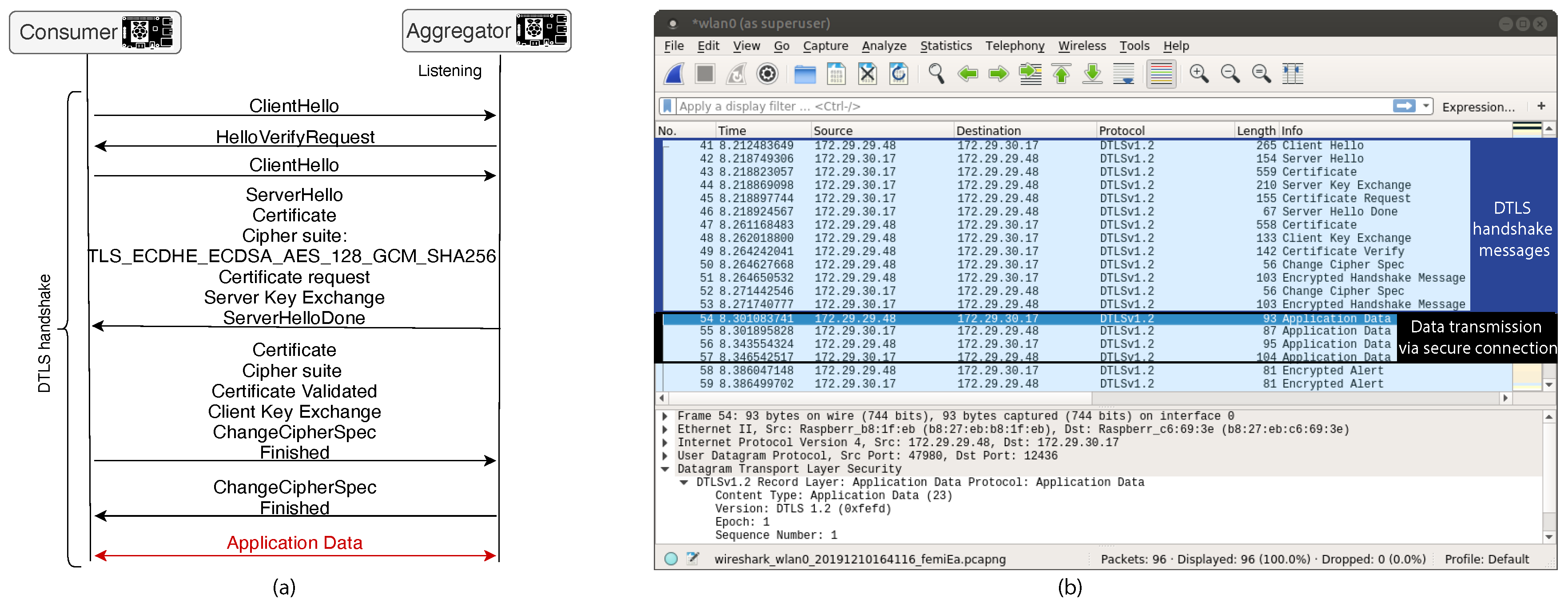
Sha sha stands for security hashing algorithm and it s probably best known as the hashing algorithm used in most ssl tls cipher suites. Find all of the sha 1 certificates in your network regardless of issuer by using scanning tools like discovery. Asa supports the sha 2 signature algorithm starting from 8 2 5 pre 8 3 releases and 8 4 1 post 8 3 releases onwards cisco bug id cscti30937.