Stuxnet Network Diagram R
Free Printable Stuxnet Network Diagram R

Dealing with multiplex links interactive and animated visualization for longitudinal networks.
Stuxnet network diagram r. Flow diagram of server service. Cy 0 wrote. Three packages are of interest in r. Kolaczyk and g??bor cs??rdi s statistical analysis of network data with r 2014.
Igraph for data preparation and plotting ggraph for plotting using the grammar of graphic and networkd3 for interactivity. I want to create a network by using r but i only have a table that contain otu id and the abundance value of two samples only. Luke a user s guide to network analysis in r is a very useful introduction to network analysis with r. Connections between nodes are represented by links or edges.
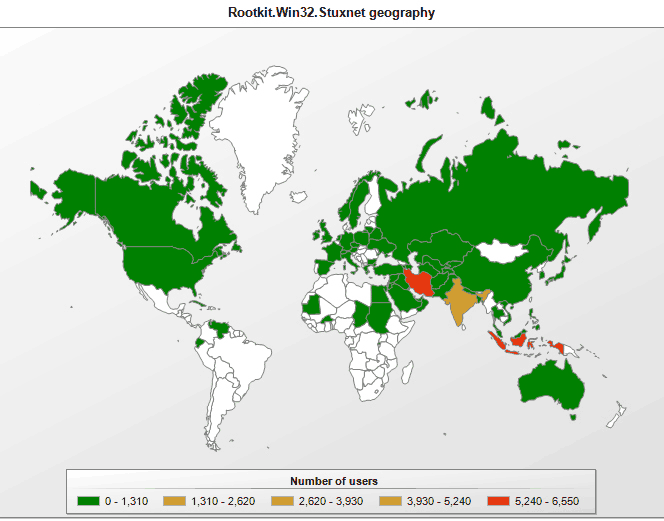
Stuxnet worm is an example of a recent malware first detected in july 2010. Each entity is represented by a node or vertice. First it analyzed and targeted windows networks and computer systems. Description as radialnetwork converts an r hclust or dendrogram object into a list suitable for use by the.
Greatly appreciated to any. Luke covers both the statnet suit of packages and igragh. And visualizing networks on geographic maps. Networkd3 package tools for creating d3 network graphs from r description creates d3 javascript network tree dendrogram and sankey graphs from r.
And israel are the most common suspects specifically to. If can which package can be used or any other software. Stuxnet was a 500 kilobyte computer worm that infiltrated numerous computer systems. Stuxnet the powerful malware that wormed its way in and hobbled iran s uranium enrichment efforts infiltrated the secure networks of the nuclear program via trusted partners newly public.
Datacamp offers a good online course on th. Its purpose was not just to infect. The contents are at a very approachable level throughout. 1 this virus operated in three steps.
More advanced is eric d. We present extensions to the popular metasploit framework to ease network based. Network diagrams or graphs show interconnections between a set of entities. Stuxnet is an extremely sophisticated computer worm that exploits multiple previously unknown windows zero day vulnerabilities to infect computers and spread.
Construction of network diagrams by using r. As radialnetwork convert an r hclust or dendrogram object into a radialnetwork list. The worm having infiltrated these machines began to continually replicate itself. The stuxnet worm first emerged during the summer of 2010.
In the case of stuxnet there s a great story. As the story goes the stuxnet worm was designed and released by a government the u s.