Network Diagram Kerberos Firewall
Free Printable Network Diagram Kerberos Firewall

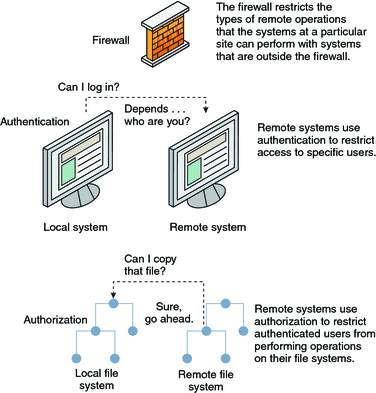
The basic firewall network diagram template demonstrates how firewalls can be integrated into a network.
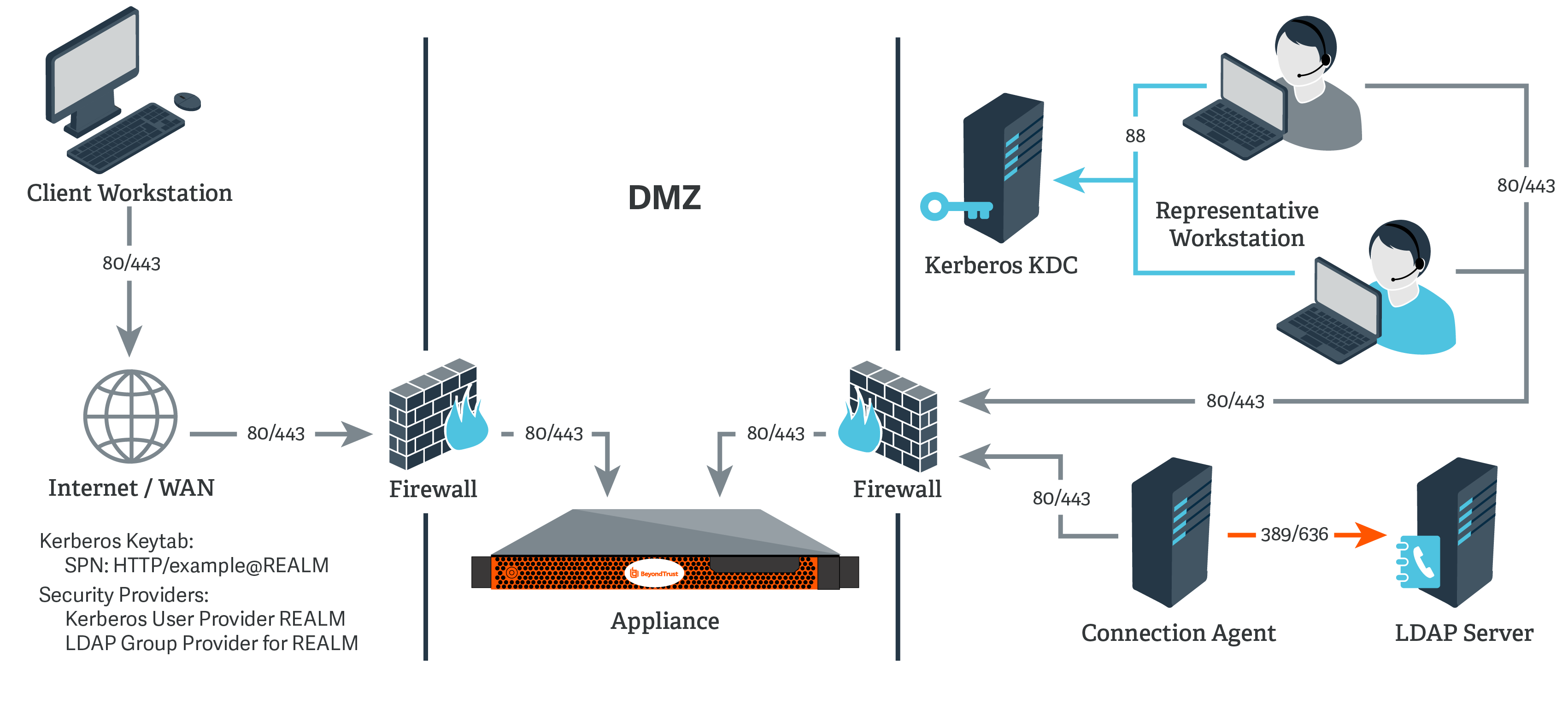
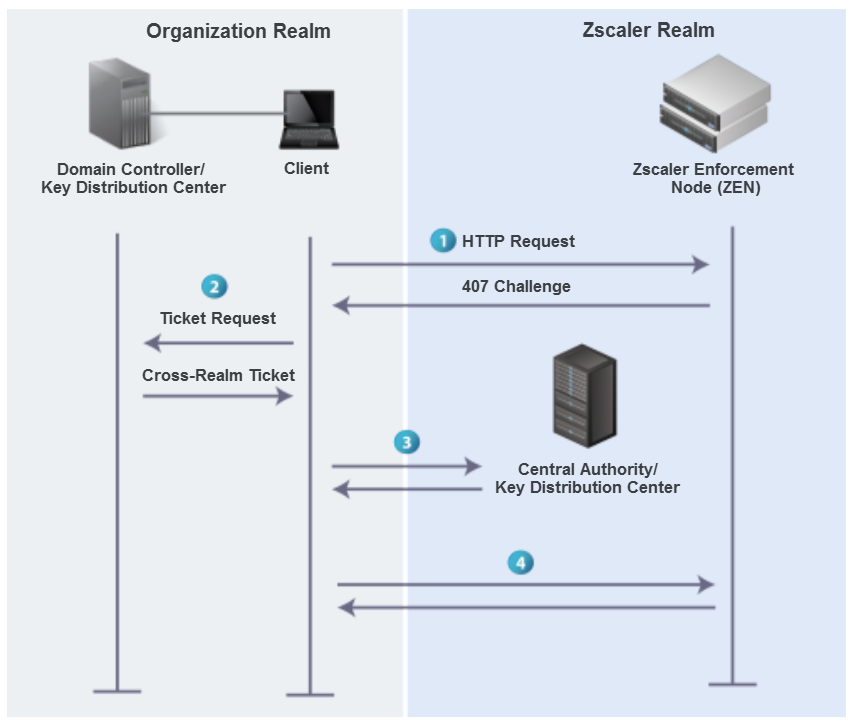
Network diagram kerberos firewall. Firewall provides network boundary protection by separating an internal network from the public internet. Figure 1 shows three different client connection types and also includes all display protocols. S designed to simply provide the information retrieval service that you need without the complications involved with kerberos authentication. This requires either that you have a slave kdc outside your firewall or you configure your firewall to allow udp requests into at least one of your kdcs on whichever port the.
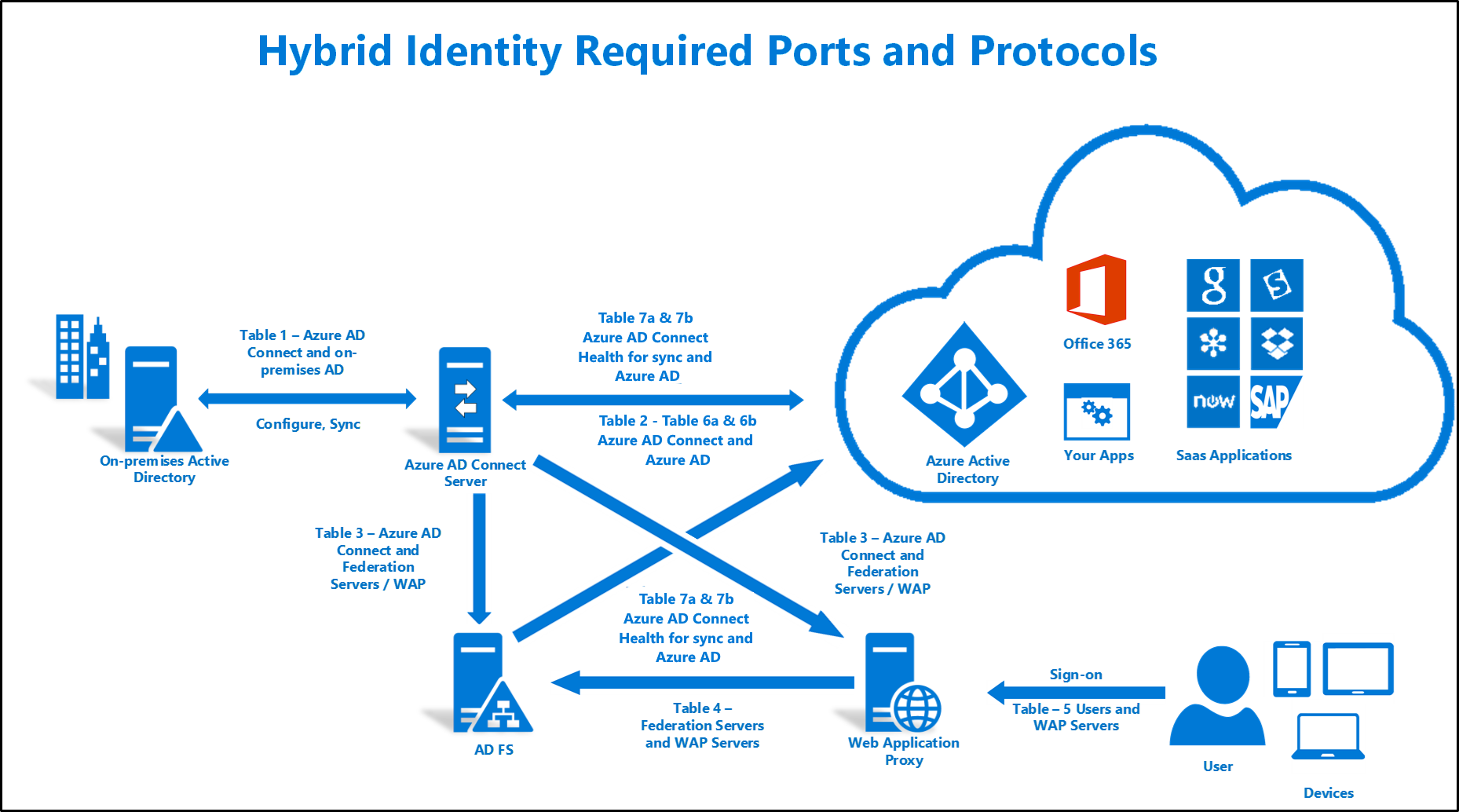
Network access control comprises of two main components. Each subset of figure 1 focuses on a particular connection type and display protocol use. Radius is a popular mechanism for providing central authentication in the network. Network firewalls are a software appliance running on general purpose hardware or hardware based firewall computer appliances that filter traffic between two or more networks.
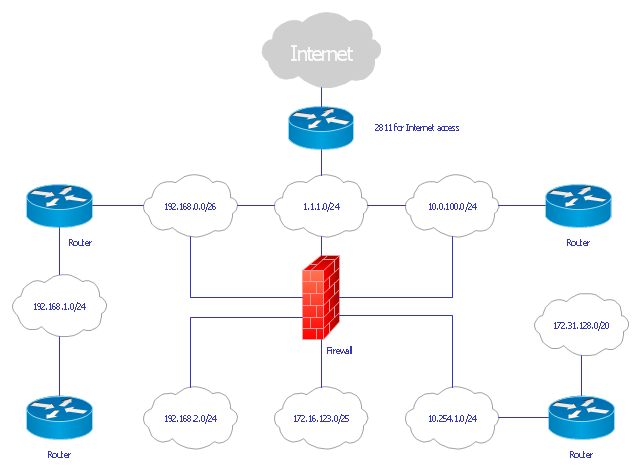
But many times multiple devices are required to completely secure a network. For example many firewall implementations include items discussed earlier in this chapter such as intrusion detection and ip security. The example uses visio like network diagram shapes. Use mydraw to create your own network diagram designs.
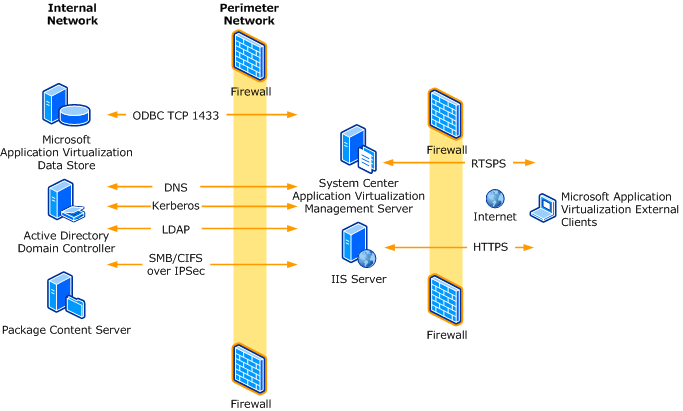
Much of the information on this page while. For computers connected to the internet do not use kerberos as an authentication method. Ports used kerberos is primarily a udp protocol although it falls back to tcp for large kerberos tickets. Kerberos and ssh through firewalls and nats.
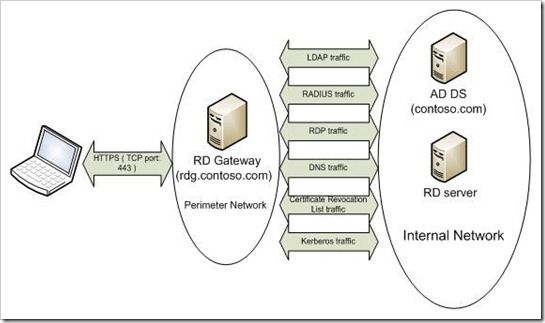
We use cookies to allow us to automate the access and the data entry functions of our website and to correlate. Horizon 7 network ports with all connection types and all display protocols. Kerberos clients need to send udp and tcp packets on port 88 and receive replies from the kerberos servers. Network diagrams and maps.
S designed to simply provide the information retrieval service that you need without the complications involved with kerberos authentication. 6 4 configuring your firewall to work with kerberos v5 if you need off site users to be able to get kerberos tickets in your realm they must be able to get to your kdc. This may require special configuration on firewalls to allow the udp response from the kerberos server kdc. Different subsets of this diagram are displayed throughout this document.
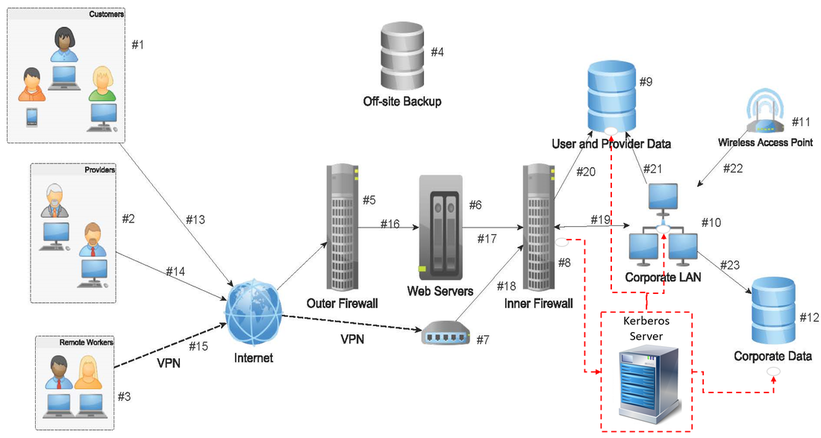
Network firewalls are a software appliance running on general purpose hardware or hardware based firewall computer appliances that filter traffic between two or more networks. User authentication and network boundary protection. The protocol was named after the character kerberos or cerberus from greek mythology the ferocious three headed guard dog of hades.