Personal Network Attack Diagram
Free Printable Personal Network Attack Diagram

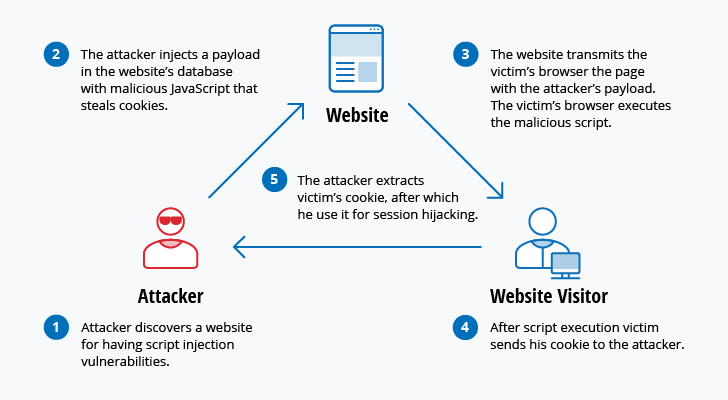
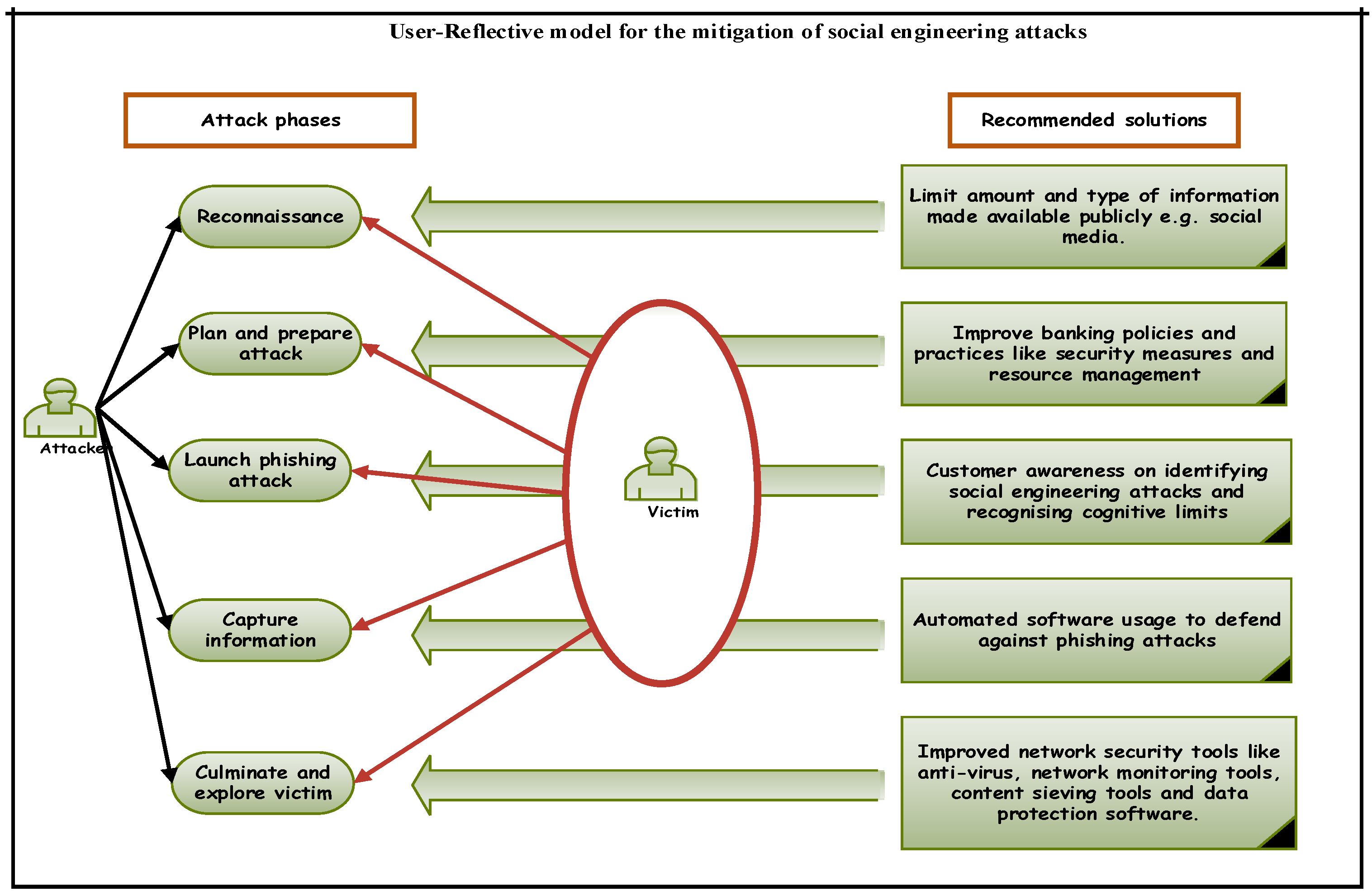
A cyberattack is any type of offensive maneuver that targets computer information systems infrastructures computer networks or personal computer devices an attacker is a person or process that attempts to access data.
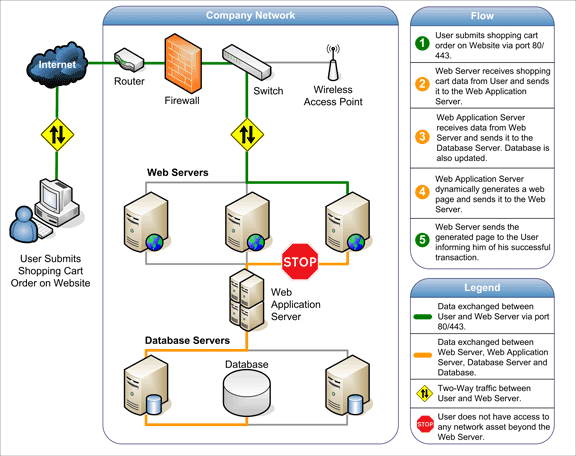
Personal network attack diagram. Internet and network attacks. Before starting to create a two tiered networking system remember the most important concept underlying the networking process. Internet and network attacks malware malicious software common types of. A distributed denial of service ddos attack is a malicious attempt to disrupt normal traffic of a targeted server service or network by overwhelming the target or its surrounding infrastructure with a flood of internet traffic.
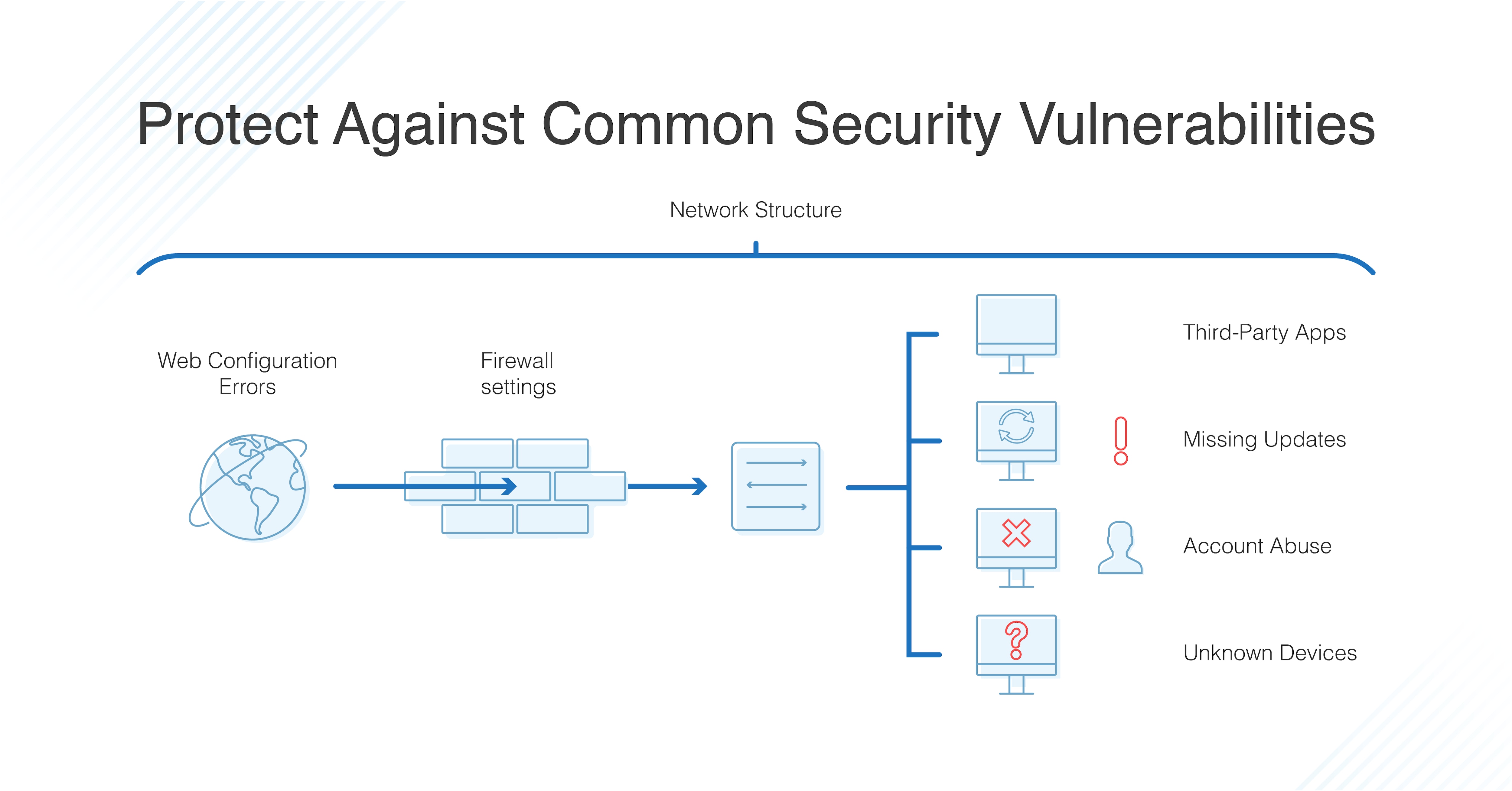
The software s interface is very familiar to that of microsoft word 2007 in terms of button layout and menus. Many times the size of the ip packet is greater than the maximum size allowed by the underlying network such as ethernet token ring etc. In the field of information technology they have been used to describe threats on computer systems and possible attacks to realize those threats. Other routes for network attacks include open ports conventional email attachments with viruses and trojan horses or drive by attacks when visiting malware infected websites.
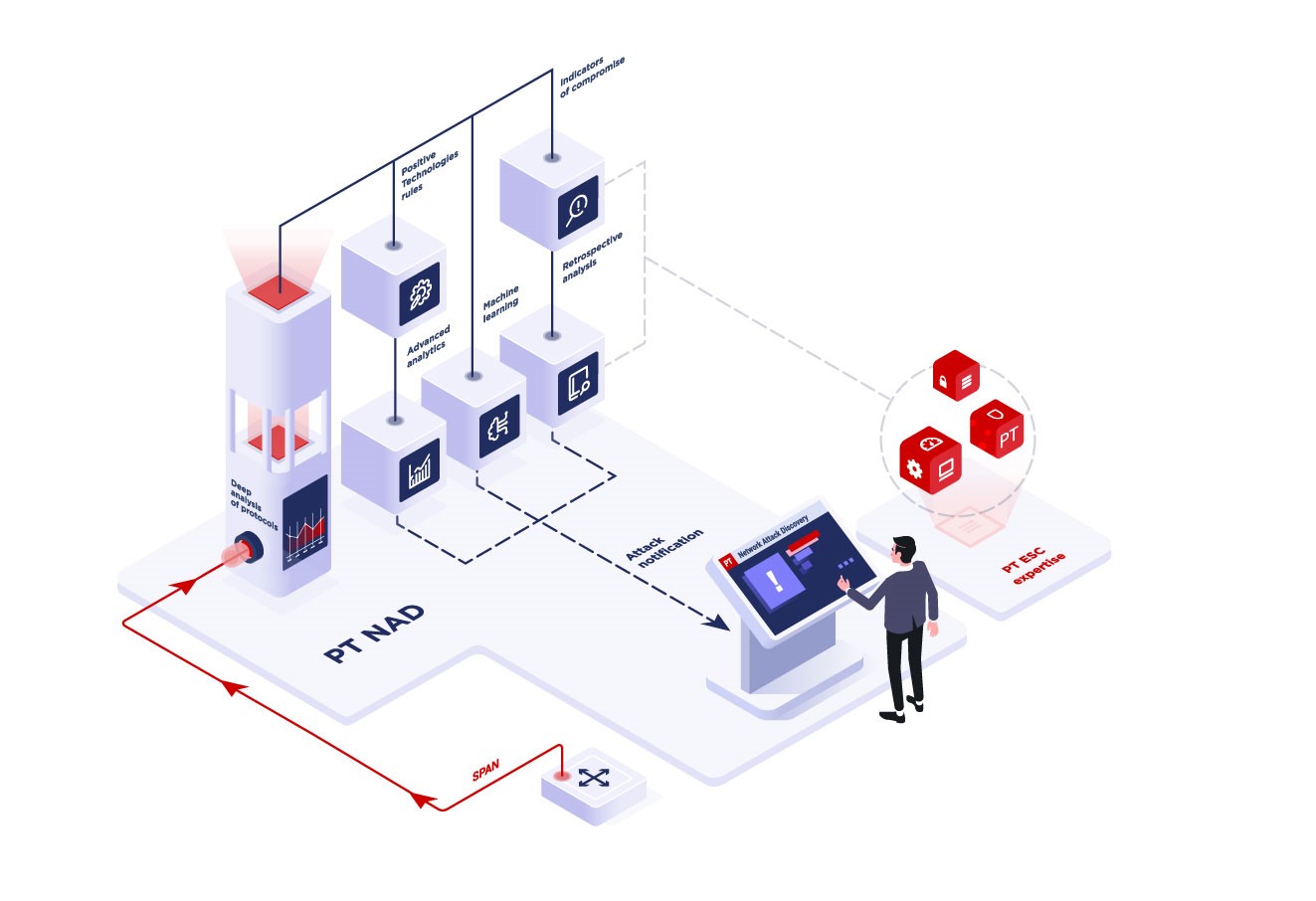
Integrated network mapping solutions are clearly superior to the combination of network. Because of its extensive menu and icon layout it is very easy to use due to its drag n drop functionality making this software easy to learn and use on a daily. In computers and computer networks an attack is any attempt to expose alter disable destroy steal or gain unauthorized access to or make unauthorized use of an asset. It is critical that you clearly identify your network contacts develop a personalized networking plan and build an administrative process to manage it all.
Today i will focus on what is known as denial of service dos attacks. Internet and network attacks. Create your own diagrams like this for free with coggle. However their use is not restricted to the analysis of conventional information systems.
Attack trees are conceptual diagrams showing how an asset or target might be attacked. In my last article on how to prevent threats and attacks on your cisco network i explained in detail the various reconnaissance techniques that an attacker can exploit. Firewalls and antivirus software are recommended for blocking these routes. I m very disappointed to admit that in our days this type of attack is one of the most common attacks found in the network community.
These scan the network and integrate the identified devices directly in network diagrams and maps so called auto mapping generating the network maps automatically. Gone are the days when you could just scan for signatures. Attack trees have been used in a variety of applications. In addition to the combination of scanners and mapping tools there also exists complete network mapping solutions.
Ddos attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Ask your network contacts for their help not for a job.